Ransomware Recovery Blog
The Coveware team prides itself on keeping up-to-date, 24/7 with every aspect of ransomware and its possible threat to your business.
If you need immediate help with a specific ransomware strain, or are curious about the threat landscape of your industry, then let us know.

Nitrogen ransomware was derived from the previously leaked Conti 2 builder code, and is similar to Nitrogen ransomware, but a coding mistake in the ESXi malware causes it to encrypt all the files with the wrong public key, irrevocably corrupting them. This means that even the threat actor is incapable of decrypting them, and that victims that are without viable backups have no ability to recover their ESXi encrypted servers. Paying a ransom will not assist these victims, as the decryption key/ tool will not work.
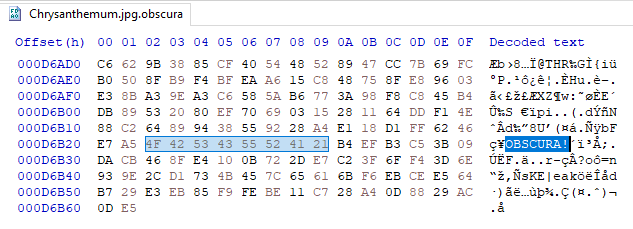
Discover how Obscura ransomware corrupts encrypted files beyond recovery, and why technical validation is key to smart ransom response decisions
The percentage of companies choosing to pay ransoms dropped significantly, while threat actors shift their tactics in response to decreasing profits.
Several ransomware groups used highly targeted social engineering tactics to create a major impact across several industry sectors in Q2 2025.
The Ransomware-as-a-service (RaaS) model has not recovered from law enforcement disruption, and the entrance of novice actors along with non-Russian state-linked cybercriminals has led to uncertain outcomes for victims.
2024 was a banner year for Law enforcement agency actions against ransomware and cybercrime groups. Will the new administration ensure this momentum continues?
A recent Australian Financial Review (AFR) article contained statistics about ransomware payment trends that require some deeper inspection.
In Q3 2024 Law enforcement actions disrupted infrastructure and publicized the identity of several prolific ransomware threat actors
Unaffiliated ‘lone wolf’ threat actors carry out a greater share of attacks as they attempt to obfuscate their identity in Q2 2024.
RaaS developers were caught cheating their affiliates, shaking the trust in the RaaS model following several high profile law enforcement actions.
A lower percentage of ransomware victims are paying, as new regulations begin to elicit more and more public disclosure of ransomware incidents.
In Q3 2023 a series of ransomware attacks by similar threat actors created headlines and blurred the lines of attribution.
As ransomware affiliates are paid less frequently, they have adapted their strategies to compensate for the shifting dynamics of cyber extortion.
Ransomware threat actors are moving back up-market in search of lost profits as the cyber extortion economy seeks to halt its contraction.
Only 37% of ransomware victims paid a ransom in Q4, a record low as security and backup continuity investments pay off.
The conviction of a high profile security executive who paid to suppress a data leak has created a new dimension of risk for security executives.
Ransomware actors became more fluid in Q2 2022 as attribution becomes harder, and fewer victims succumb to paying cyber criminals.
During a recent HSGAC hearing, Coveware had the opportunity to provide testimony on how ransomware attacks are impacting US companies, and the importance mandatory reporting.
Less Victims of Ransomware are Paying, even as Cybercriminals Shift from Big Game to Big Shame Hunting
The long term impact of sanctions on Russian unemployment has the potential to increase the volume of future Ransomware attacks.
Ransomware as a service groups are shifting their tactics as enterprises become harder targets, and law enforcement pressure mounts.
As the Ransomware attacks continue, the direction and growth of the RaaS model is following a traditional innovation trajectory.
Ransomware attacks continued to proliferate in Q3 as governments and law enforcement ratchet up the pressure of the cyber extortion economy
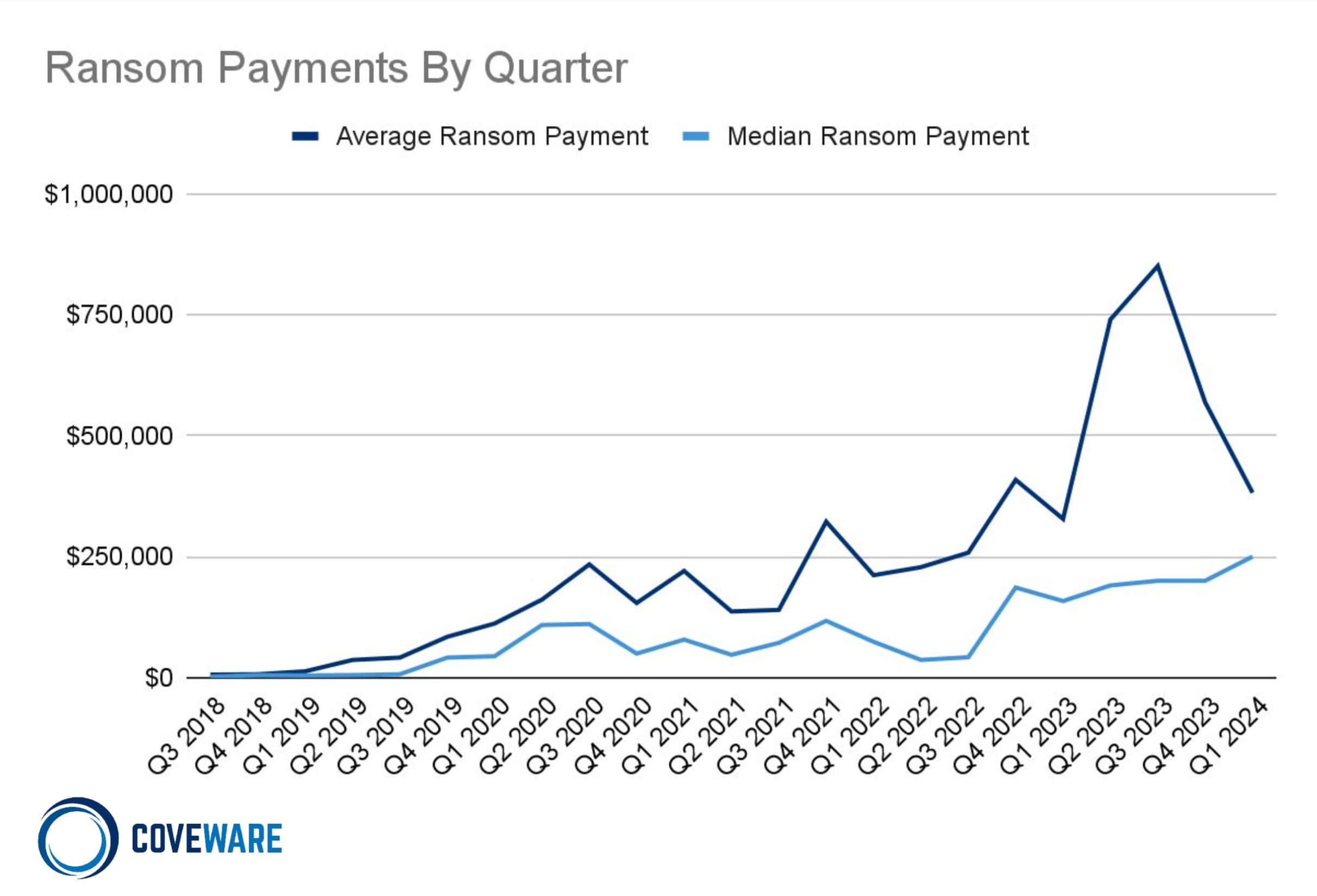
Ransomware payment amounts declined in Q2 as several high profile attacks escalated the attention of the US government and law enforcement.
Ransomware Actors Explain in their Own Words How to Become an Expensive Target through security reports written to victims.
Ransomware attacks continued to proliferate in Q1 2021 as several common but unpatched software vulnerabilities created a fresh supply of compromised network access to ransomware affiliates.
See how doxxing victims are distributed across industries, company sizes, and revenue tiers. Find Coveware’s data and analysis on doxxing trends in Q4.
Coveware’s Q4 Ransomware Report finds that fewer companies are paying criminal extortionists that are holding stolen data for ransom.
See the realities of ransomware attacks on small and medium-sized professional service firms and what factors lead to increased vulnerability.
Ransomware attacks in Q3 2020 were marked by a larger reliance on stolen data. During the quarter, Maze sunset their operations while Ryuk restarted their campaign.